Subscribe Here!
Communication Service Providers (CSPs), in a way, are the “backbone” of global operations across industries, ensuring continuous network availability and data confidentiality given the sensitivity of the data they handle and transmit. New-age technology like Telco Cloud empowers CSPs to gain the highest levels of agility, flexibility, and scalability.
But shifting to a next-generation cloud architecture can be a double-edged sword. Softwarization and cloudification of the telco infrastructure increase the security complexities making it difficult for CSPs to handle sensitive workloads or employ cloud applications and services with confidence.
So, what should CSPs do about it?
In our experience, the right path to Telco Cloud security entails a better safe than sorry approach. Why? The adaption of new technologies such as SDN (Software Defined Networks), APIs (Application Programming Interfaces), and DevOps increases the number of connected devices and services, thereby expanding the attack surface, potentially exposing the Telco Cloud to more cyberattacks.
This blog, basis our experience in handling leading CSPs’ infrastructure, highlights security best practices and risk management imperatives necessary to proactively safeguard the Telco Cloud.
Telco Cloud Amps Up the Need for Security
As the Telco Cloud is truly a transformational (not just incremental) advancement to existing telecom infrastructure, CSPs will need to relook at their current security posture. There will be new questions about security systems, processes, and governance models.
For instance, the interconnected nature of cloud technologies with existing operational and business support systems (OSS/BSS) creates an extensive infrastructure, expanding the overall attack surface. Furthermore, the cloud breaks down data silos and drives collaboration, but the lack (or absence) of data governance can lead to potential data breaches or unauthorized access.
To de-risk the Telco Cloud, our experience suggests that CSPs need to first and foremost focus on traffic flow security. It is crucial to protect the data from attacks originating from all directions: traffic flowing in and out and within the Telco Cloud. Implementing a defence-in-depth security strategy prevents attackers from reaching the network’s traffic.
Similarly, CSPs must consider a security-by-design approach to build long-term resilience for securing new architectural requirements. A security-first design reduces an attacker’s lateral movement across domains, including,
- Internal IT domains (e.g., corporate apps, e-mail, web browsing, social media)
- Support systems (e.g., OSS/BSS, Management and Network Orchestration (MANO) systems)
- Customer-facing domains (e.g., channel portals, websites, call centres)
- Network domains (e.g., VNFs, servers, routing, transport, base stations, IoT devices)
Telco Cloud Security Imperatives: Make it Harder for Attackers
As the Telco sector moves away from proprietary hardware models to host network functions in software form and in the cloud, inadequate design and misconfigurations are often the leading cause of security breaches. The good news is we know the security must-haves to make the Telco Cloud more secure.
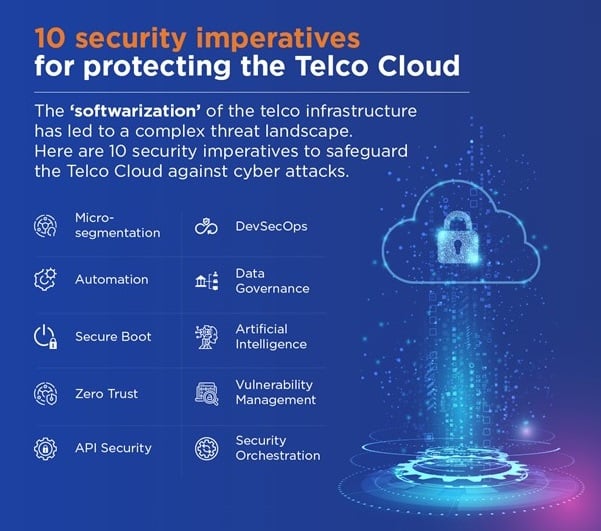
- Create Micro Segments: Micro-segmentation isolates applications at four levels: physical, network, service, and user levels, securing them individually with app-specific policies. These granular security settings allow applications to co-exist in the same virtualization environment but create isolation to reduce the scope of traffic flow and contain the spread of data breaches.
- Automate Provisioning: It’s no surprise that human related activities are considered one of the weakest links in security. To eliminate human errors and recover from attacks faster, leverage zero touch provisioning and Infrastructure-as-Code (IaC) scripting. It should include security architecture design and identity policies to configure telco infrastructure.
- Use Hardened and Secure Boot: Provision only attested hosts to Telco Cloud environment by leveraging host profile (golden image) templates and the Pre-boot Execution Environment (PXE) to add known hosts to the virtualized environment. Enable secure boot on the host to ensure that only digitally signed codes are allowed to run.
- Apply Zero-Trust: The model relies on three core principles: never trust, always verify; assume breach and; apply least-privileged access. It assumes that a network is always compromised, and trust needs to be rebuilt. Combining a zero-trust model with identity and access management systems continuously verifies a user’s authenticity before allowing access, decreasing the severity of attacks.
- Secure APIs: APIs allow various apps and services to communicate within and outside of the Telco Cloud ecosystem, increasing the attack surface. Some of the key API security mechanisms involve:
- OAuth: OAuth is a token-based authorization framework that allows third-party services to access data without exposing credentials, establishes trusted identities, and controls access to services.
- Data encryption: All data, especially personally identifiable data, should be encrypted using Transport Layer Security (TLS) to avoid data exfiltration.
- API threat modelling: It facilitates a continuous cycle for assessing, mitigating, and preventing application vulnerabilities in an automated yet controlled fashion.
- Move from DevOps to DevSecOps: Focus on security components such as identity, authorization, cryptography, key management, audit/log, and protocols. They can be applied within every micro-service during the development process.
Since microservices are decoupled, vulnerabilities and bugs are often limited to a specific component instead of the entire application. Vulnerabilities can be fixed by simultaneously implementing static analysis security testing (SAST) and dynamic analysis security testing (DAST).
- Establish Data Governance Framework: As telecom networks, especially 5G, increasingly become open and distributed, the number of systems and services is set to increase exponentially. The Telco Cloud enables operators to break down data silos to make it accessible, but also makes networks vulnerable. A data governance model takes proper account of how data is generated, stored, analysed, and protected.
- Use Artificial Intelligence (AI) and Automation: Although AI-powered automation saves time and money and accelerates time to market, it introduces new privacy and regulatory compliance risks. It is possible for an attacker to access an AI algorithm and direct it to make incorrect decisions, resulting in negative consequences.
It is recommended that CSPs implement security measures powered by artificial intelligence (AI) to safeguard their ecosystem. This includes incorporating a security framework that effectively manages AI use cases.
- Vulnerability Management: Unpatched applications and discrete network elements across legacy systems are a common source of security breaches. Patch management fixes vulnerabilities present in software and applications and adds new features to ensure devices on the network are compliant.
Maintaining golden (or master) images with the latest patches and configuration helps to rebuild network elements on the fly. Vulnerability assessment tools and source code scanners automate the testing of deployment pipelines to uncover – programming issues, patching gaps, and configuration issues.
Security Orchestration and Management: Security teams work on numerous security tools to mitigate cyber threats. These fragmented tools create a challenge in identifying the threats, so teams must manually work against each security incident.
The high volume of security alerts generated by these tools makes it difficult to respond to security threats across various systems and use cases. In such situations, security orchestration can integrate multiple tools to simplify security management functions such as:
- Posture: Provides an accurate, up-to-date view of all network elements.
- Compliance: Drives security policy consistency in a controlled deployment.
- Reports and Metrics: Known exemptions and potential areas of exposure.
- Prevention: Management by exception focused on anomalies (e.g., whitelist enforcement)
- Response time: It prioritizes threats, makes recommendations, and automates future responses, thereby reducing the time it takes to mitigate them.
In Summary
While the Telco Cloud enhances network flexibility and scalability, it also expands the attack surface and increases security complexities. To mitigate risks, CSPs must adopt a security-first approach and prioritize traffic flow security. By following these best practices, CSPs can proactively safeguard the Telco Cloud, ensuring the confidentiality, availability, and integrity of their services and data.
Tata Communications Transformation Services (TCTS) offers CSPs a strong foundation to safeguard business assets, meet compliance requirements, and reduce operational costs.
About The Author

Sanjeev Kumar N
Head - Security Practise and Office of CISO
Sanjeev has 20+ years of experience in the Information Technology sector and is passionate about cybersecurity. Sanjeev has extensive experience in the field of security, having provided security services and solutions across enterprises with unique and challenging business use cases. He played a key role in designing security solutions for enterprise networks, data centres, telecom, and cloud technology.






